Advance
“Advanced” refers to the use of sophisticated and proactive threat detection methods that go beyond basic security measures, enabling the identification and analysis of complex cyber threats in real time. This approach ensures the system can stay ahead of emerging attack patterns, providing a higher level of protection and resilience.
Alert
“Alert” refers to immediate notifications sent to users in real-time whenever a security incident is detected. These alerts are delivered via LINE and email, ensuring users are promptly informed of any potential threats, enabling quick response actions to minimize impact.
Adaptive
“Adaptive” describes the system’s ability to continuously adjust and respond to new and evolving threats. This capability allows Hackalert to dynamically update its detection methods, providing effective protection against emerging attack vectors and ensuring resilience in a constantly changing cyber landscape.
Hacker Alert
Pro-active Cybersecurity, ready-to-deploy Honeypot Solution. In an era where cyber threats are increasingly complex and persistent, Hacker Alert offers a proactive solution to shield your systems. Our Honeypot service is designed to detect, capture, and alert on potential attacks targeting your network.
HackAlert provides real-time notifications through LINE and email, enabling immediate response to suspicious activities. Additionally, we publish ongoing data on cyberattacks on our website, offering valuable insights to help organizations stay informed and prepared.
Services
HackAlert enhances your security posture, safeguarding your network and empowering your business to face evolving cyber threats confidently.
Proactively
Proactively Detect Cyber Threats to identify and capture unauthorized access attempts and potential cyber threats through strategically deployed honeypots, providing organizations with early detection capabilities.
Threat Alert
Enable Real-Time Threat Alerts to deliver instant notifications via LINE and email whenever suspicious activities are detected, allowing for timely incident response and reducing potential risks.
Research & Awareness
Support Cybersecurity Research and Awareness to publish anonymized attack data on our website, fostering research and knowledge-sharing on cyber threat trends and tactics.
Build Resilience
Build Resilience Against Evolving Threats to equip clients with a proactive tool that adapts to the changing landscape of cyber threats, empowering them to protect critical assets with confidence.y leaks
Technical Detection Capabilities
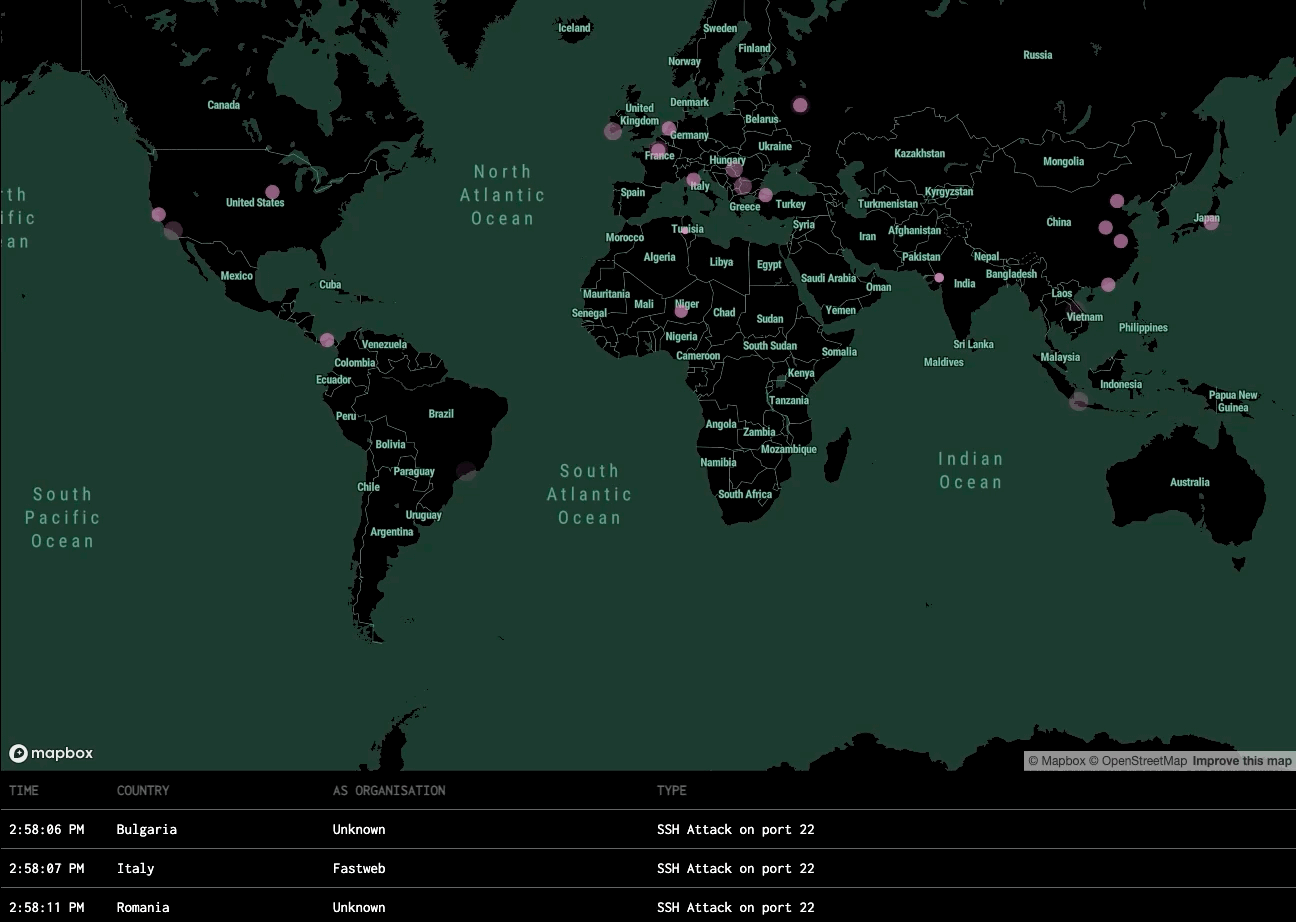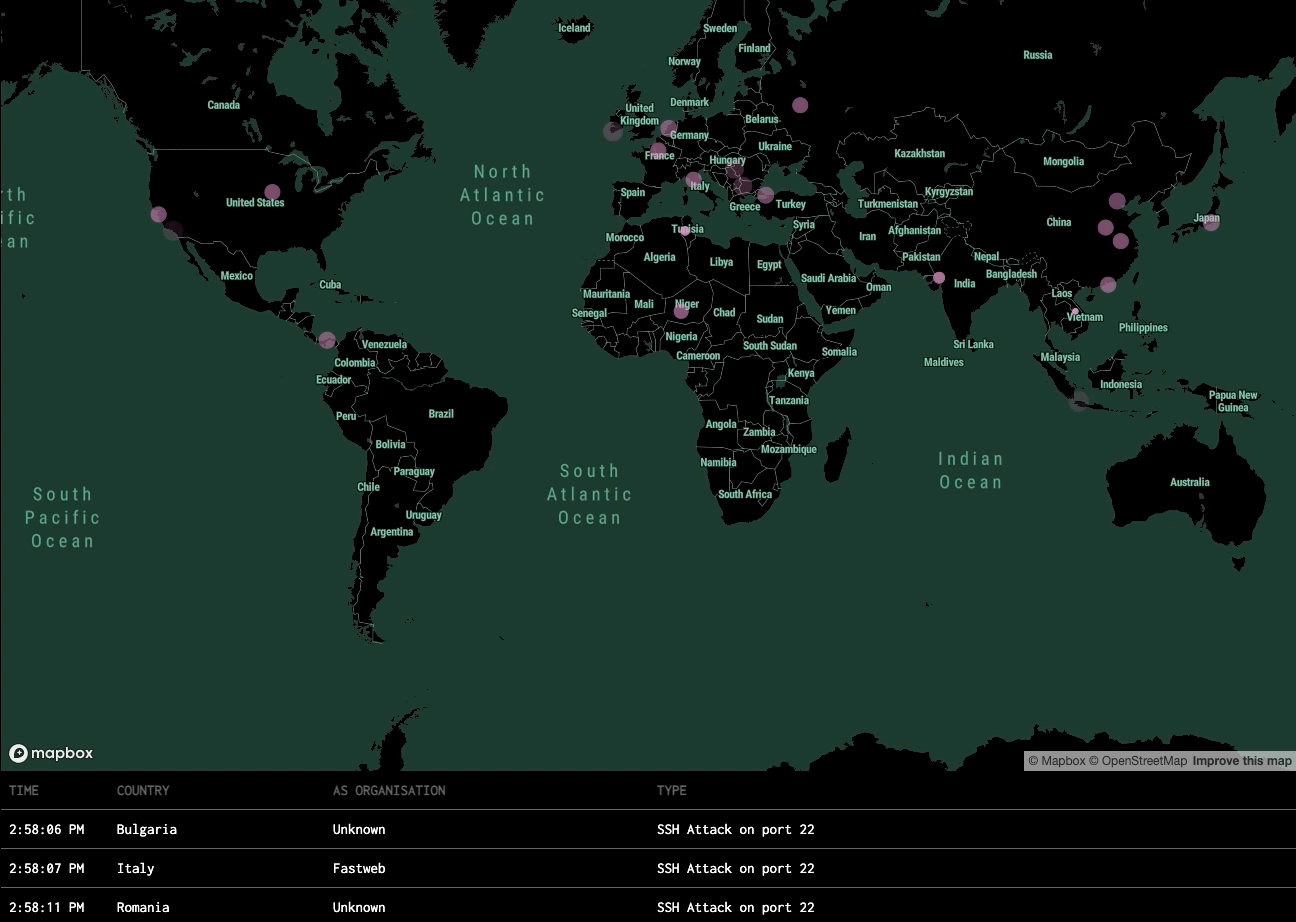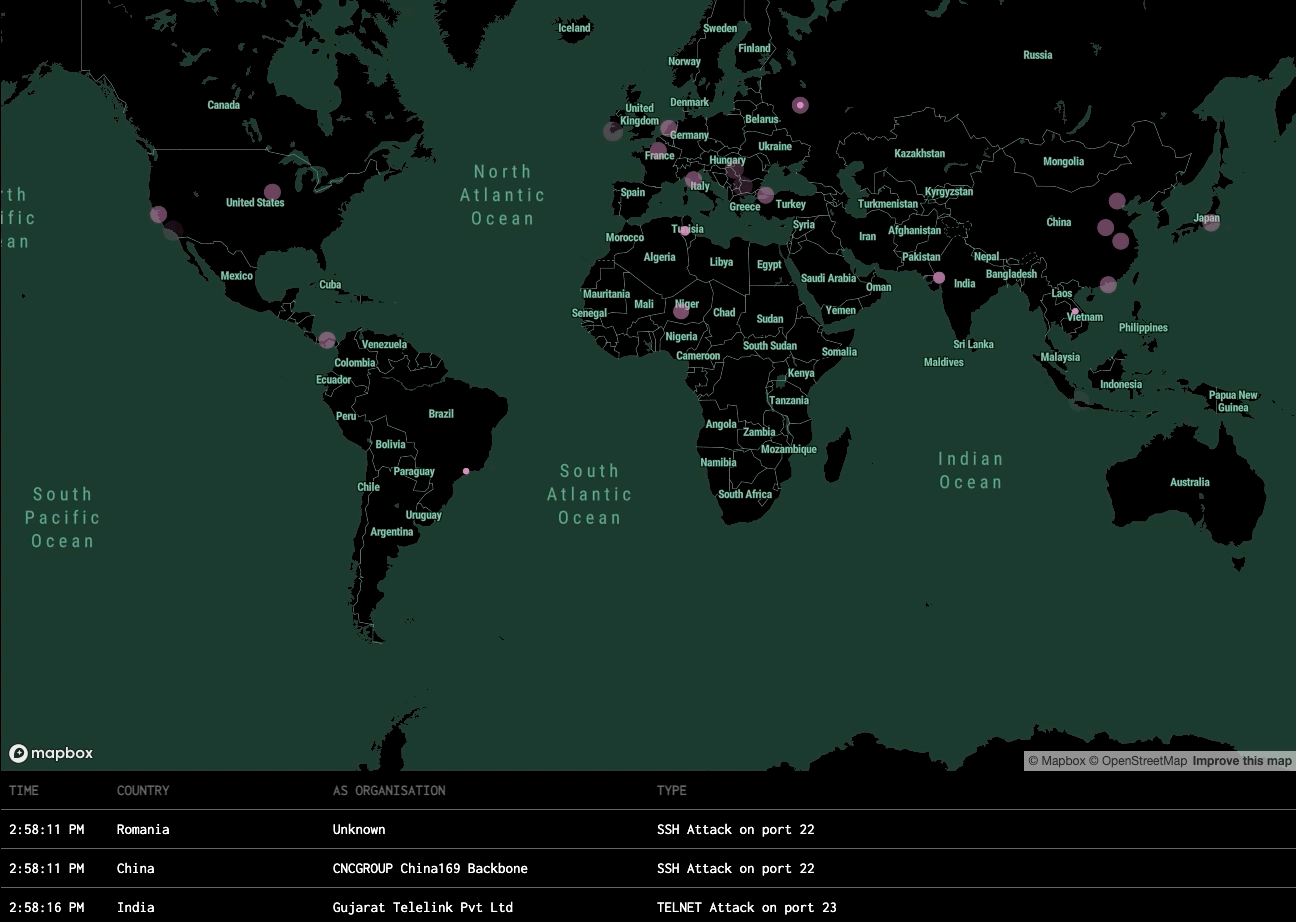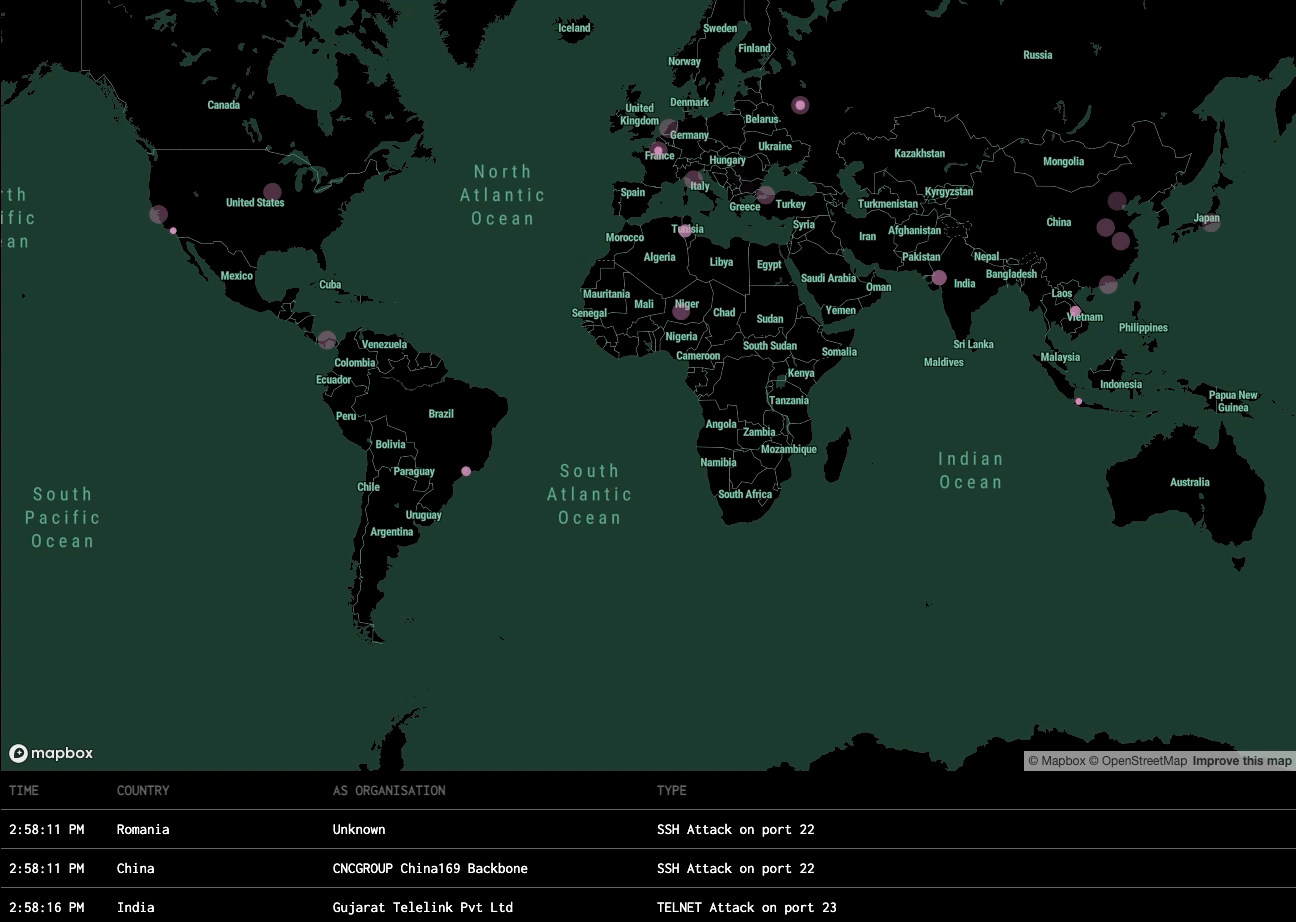
Hacker Alert is equipped with a range of honeypot techniques designed to monitor, capture, and analyze diverse types of cyber threats. Below are the primary areas of detection and the outcomes provided.

Intrusion Attempts
Detection: Detects unauthorized login attempts, brute-force attacks, and remote access probes (e.g., SSH, RDP).
Outcome: Logs every attempt, including IP address, time, and method, providing insights into potential attack sources and patterns.

Malware Deployment and Exploits
Detection: Captures attempts to exploit known vulnerabilities in services (e.g., HTTP, FTP, SMB) and attempts to deploy malware.
Outcome: Isolates malicious payloads and records details on the exploited vulnerabilities, helping organizations understand which weaknesses are targeted.
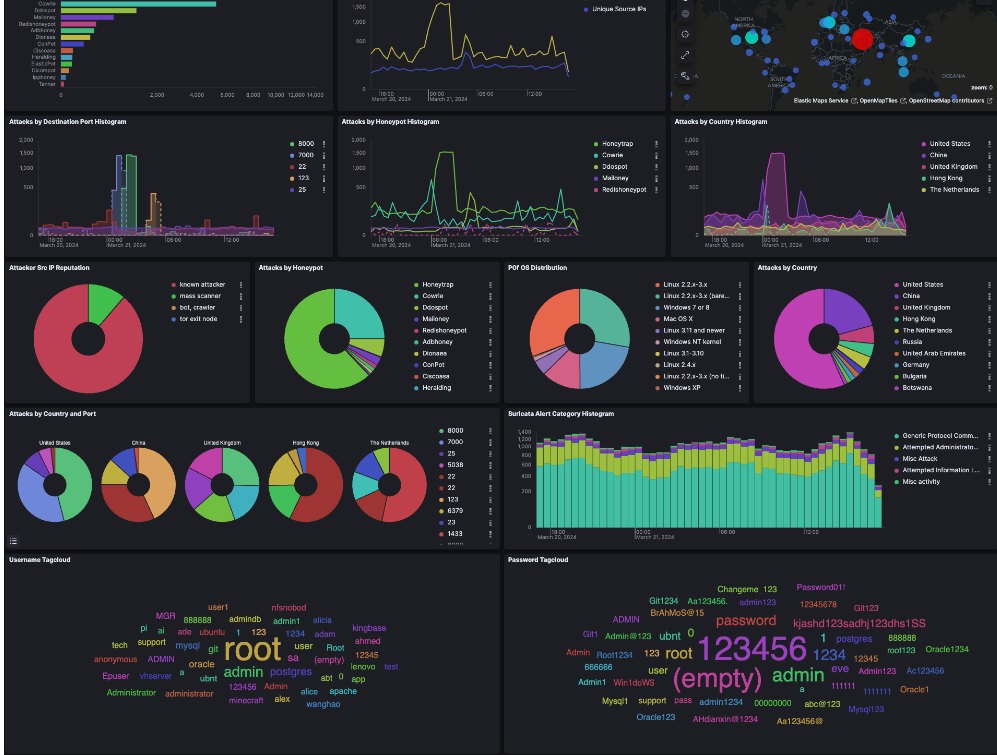
Port Scanning and Network Probing
Detection: Identifies and logs port scanning activity, which indicates an attacker mapping out network services and vulnerabilities.
Outcome: Generates a report on probing frequency, common scanning tools, and potential attack intentions, supporting preemptive security actions.
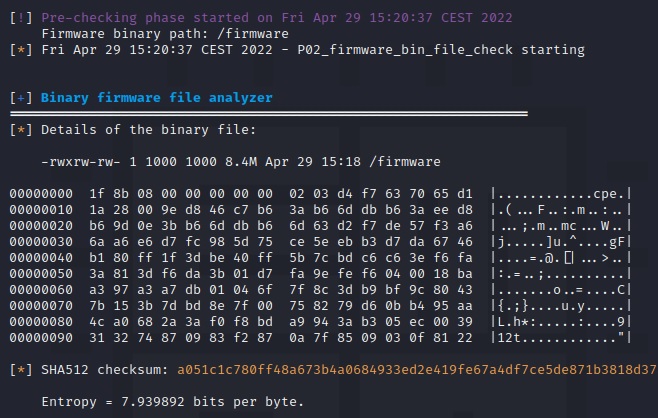
Web Application Attacks
Detection: Monitors for common web-based threats, including SQL injection, cross-site scripting (XSS), and directory traversal.
Outcome: Collects data on exploited attack vectors and attempted access to sensitive directories, helping with website and application hardening.
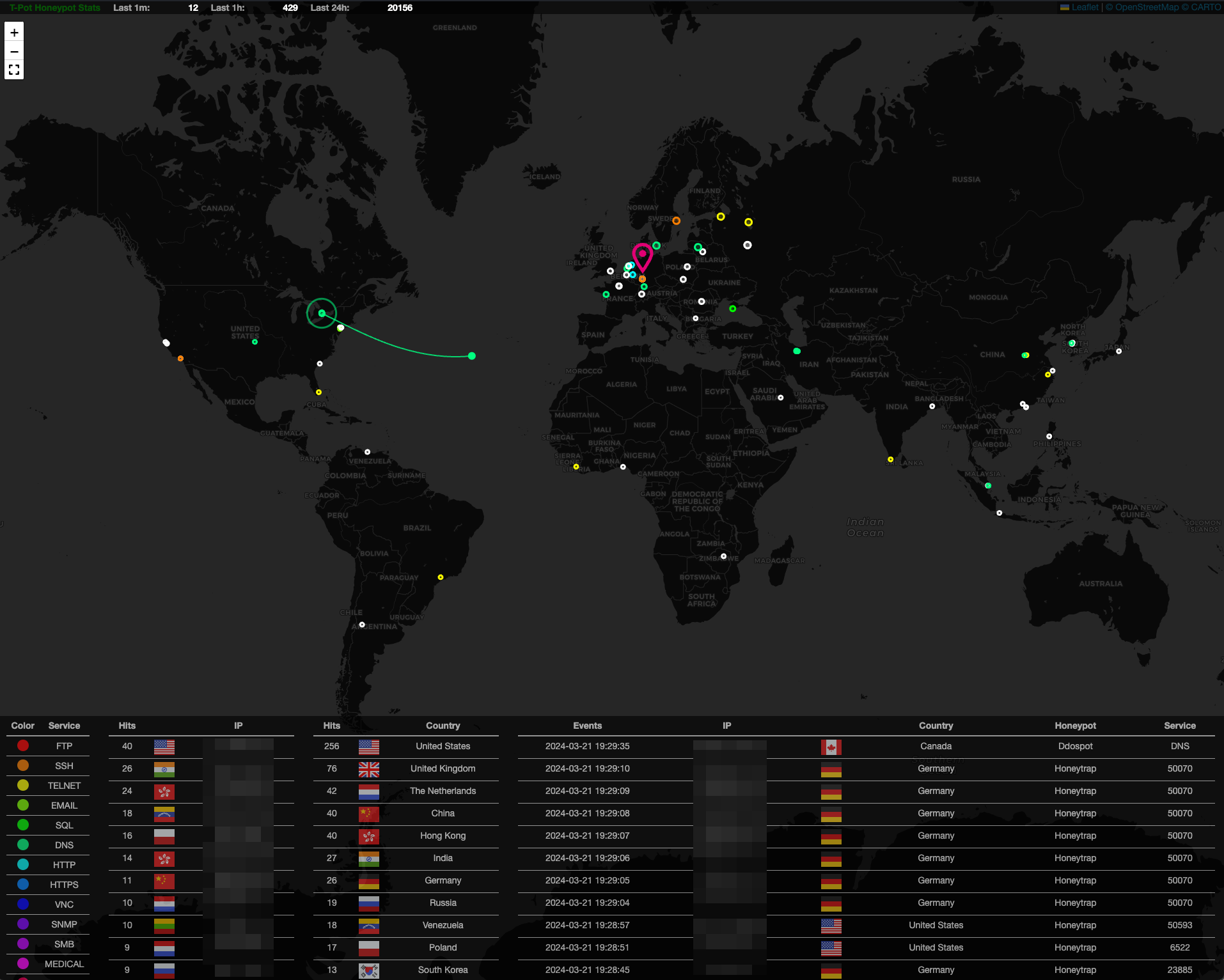
Botnet Activity
Botnet and Distributed Denial of Service (DDoS) Activity Detection: Recognizes botnet traffic, DDoS attempts, and anomalous spikes in connection requests.
Outcome: Provides alerts on potential botnet behavior and DDoS threats, including details on IP origins and request rates, allowing for immediate response.
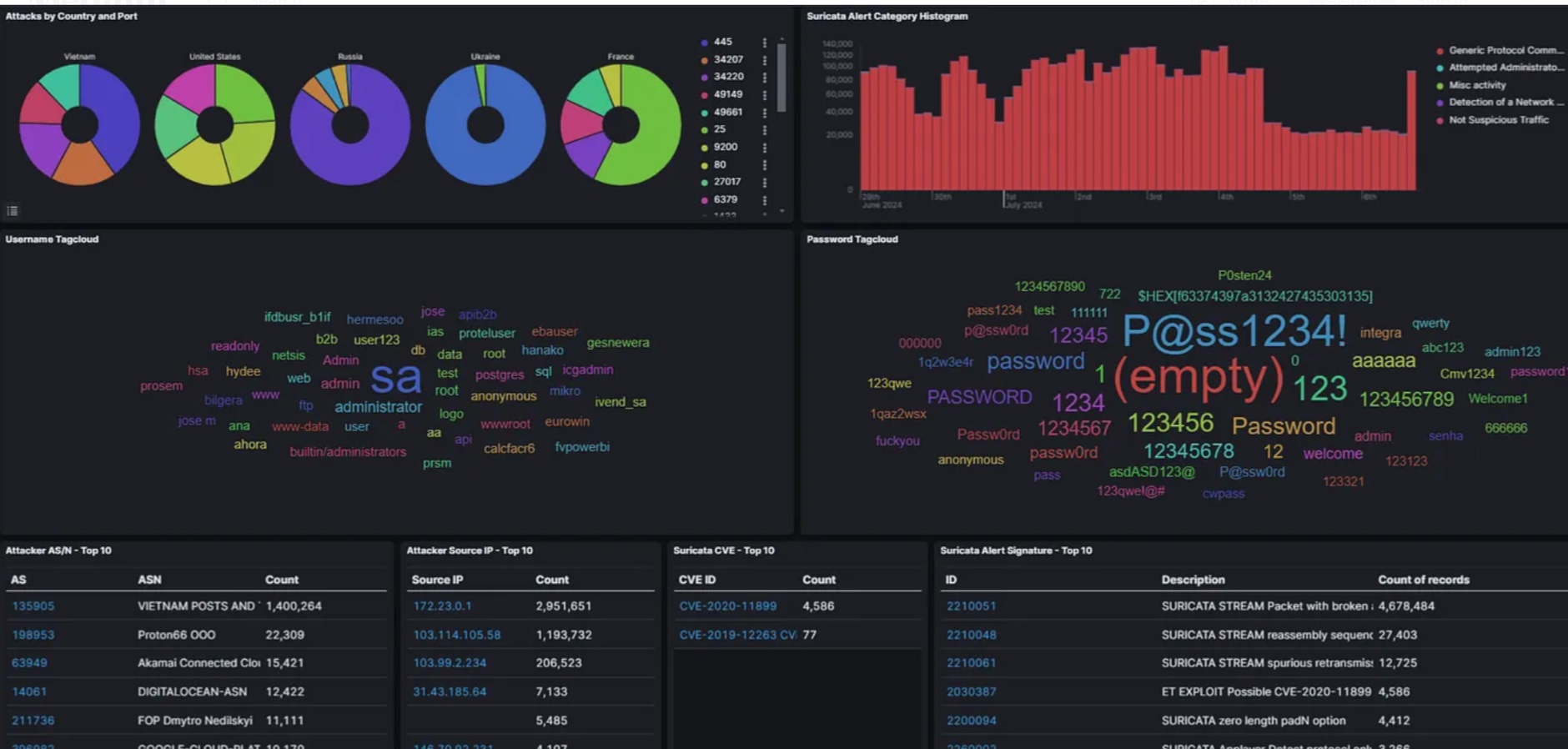
Phishing and Social Engineering
Detection: Traps attempts to connect with or misuse communication services like email, potentially for phishing or social engineering.
Outcome: Identifies phishing sources and techniques, helping secure communication channels and raising awareness of social engineering tactics.
Real-Time Alerts
Instant notifications via LINE and email, detailing threat type, origin, and action recommended.
Actionable Insights
Suggestions on enhancing security based on detected vulnerabilities and frequent attack vectors.

Comprehensive Reports
Regular summaries of captured threat data, including frequency, source countries, and common attack methods.
Step
for providing the Hacker alert service
Deployment
Monitor
Alert
Report
Hacker Alert Services




Location
48/6 Soi Chaengwattana 14, Thung Song Hong Subdistrict,
Lak Si District, Bangkok 10210
Contact
info@tunableproject.com
info@gbtech.co.th
Phone
669-4179-8888